KGB virus. Description and method of removal
- 9.11.2011, 2:27

Charter97.org website has received in its possession the virus offered by the KGB “overseer Dzima” to Maxim Charnyauski.
Maxim was to install this programme onto computers of “Revolution through Social Networks” activists hiding in Poland. The story of “recruiting” of the journalism faculty student was published a few days ago.
Our experts have analysed the received file. The program looks like a Skype installation and could have been installed on computers of the activists. We offer the results of examination and recommendations for removal of the malware:
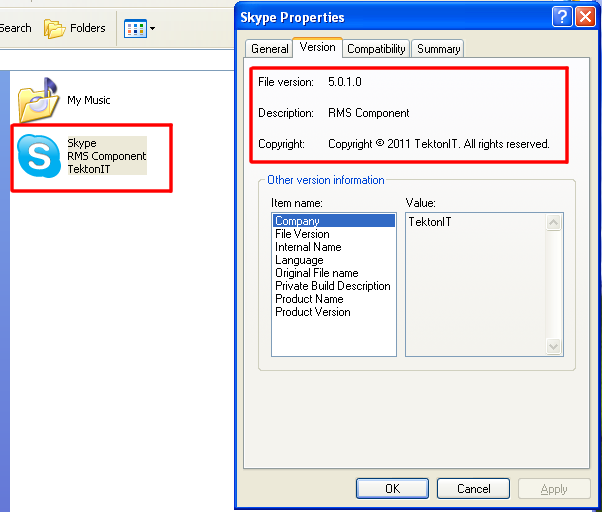
Examination of Skype.exe file (MD5: 43fe19eb0896979568b986b8e7fd0e42)
1. What kind of program is it?
The program is a self-extracting 7 zip-archive containing installer of a commercial program, known as Remote Manipulator System.
The official web-site of the program is http://rmansys.ru/
Its developer is a Russian company TeknotIT.
The icon of the program is changed for a of Skype logo image, though the rest information about the file of the application reveals its real producer and even its name.
2. If it is legal, why there are no windows?
Installation is taking place in a “passive” regime, especially designated by the developers for computer networks’ administrators, who need mass installation of such software. For this reason the program does not display the process of installation and does not ask for any confirmations from the user.
3. Where is this program installed?
Main files of the program are copes to the file directory C:\Program Files\Remote Manipulator System – Server
An additional component is installed into the system directory according to the route "C:\WINDOWS\system32\RWLN.dll"
4. Who and how can control it?
After the program started, it checks connection with the internet, sending to the address http://rmansys.ru/utils/inet_id_notify.php?test=1
Then the program sends to the server information about the system in which is it works. In this request ID of the user for whom this program had been registered, is indicated. As an ID of the user the following email is used: vbybcnthcndjcn@mail.ru .
By the way, when the name of the postbox “vbybcnthcndjcn” is typed in Cyrillic keyboard format, it gives the word “ministry”.
5. What could be done with the help of this program?
Here are some features of the program:
- Remote control access to the computer
- Remote desktop observation
- File manager
- A module for files transfer and files control
- Remote registry modification
- A terminal
- Access to the command line (an analogue to “Command-line” tool)
- Power control
- Remote program start
- Web-camera and microphone connection
- Recording of video from the desktop according to a schedule
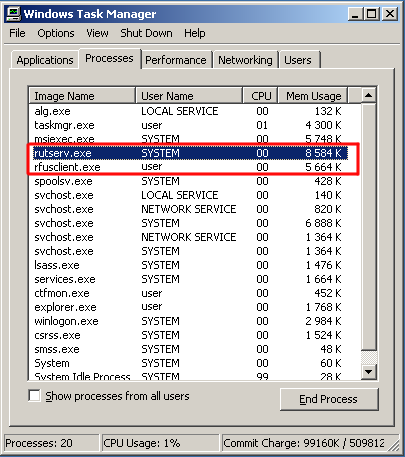
6. How one can understand that the system had been infected?
One can detect presence of the program in the system by distinctive processes it creates:
7. What about an antivirus? Will it protect the system?
The program belongs to greyware, that is, it could be used illegally to get unsanctioned access to the information stored in the computer system or network. Kasperski antivirus, for instance, detects the program as RemoteAdmin.Win32.RMS from the Riskware caregory. However to inform the user about detection of such programs requires alteration of antivirus’ default settings. Check the settings of your antivirus!
8. How to remove this program safely?
Manual removal will be the best and fastest way, as the program envisages deinstallation through Control panel.
So:
Go to the “Control panel” -> “Installation/removal of programs”. Find and delete “Remote Manipulator System.”
- Restart the system.
- Find and delete the file C:\WINDOWS\system32\RWLN.dll.
9. How to avoid being infected by this program in the future?
One should use antivirus software configured properly, and follow updates of all components of the system and browsers.
In order to deprive the future versions of "Remote Manipulator System" an opportunity to connect with the host, with the help of Notepad you can add in the end of the text file C:\windows\system32\drivers\etc\hosts the following line:
127.0.0.1 rmansys.ru









